It's time learn to capture our traffic with a tool called so we can analyze it later with
.
Let's get tcpdump on our victim.
apt install tcpdumpAnd let's see how it works. Open up another terminal and log into Victim.
docker exec -it victim /bin/bashLet's start the capture in one of the Victim terminals:
tcpdump -s 65535 -i any -v -w my_capture.pcap- s: Older versions of Tcpdump cut-off packets to 68 or 96 bytes. The ‘-s’ option is used for capturing packets with full length.
- i: Selects the interface to listen on.
- w: Saves the raw packets captured to a file instead of displaying them on the terminal.
- v: Verbose output. The more v's you use the more information will be shown in the terminal.
In the other Victim terminal let's ping the reverse-proxy and visit main reverse-proxy page:
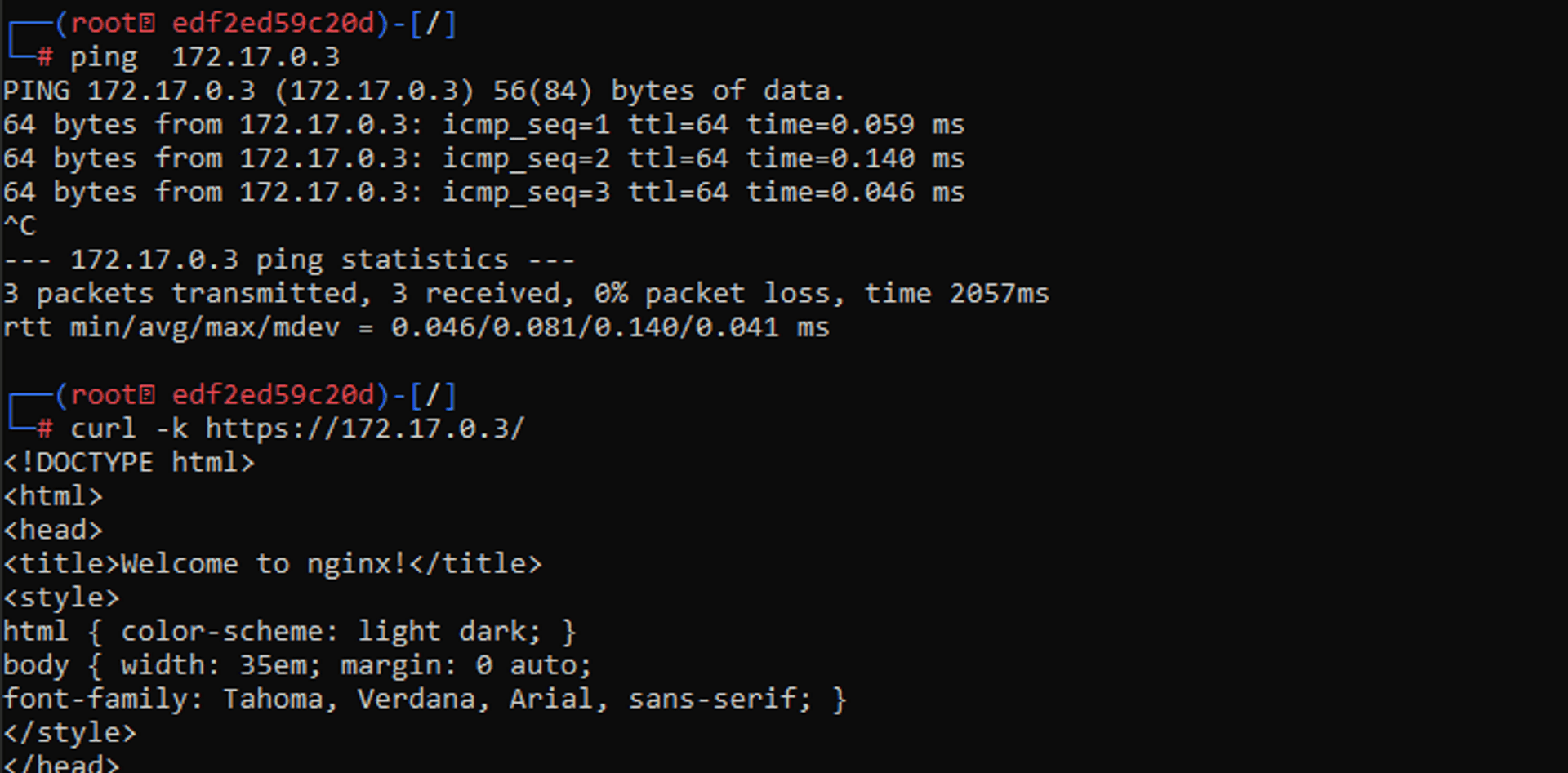
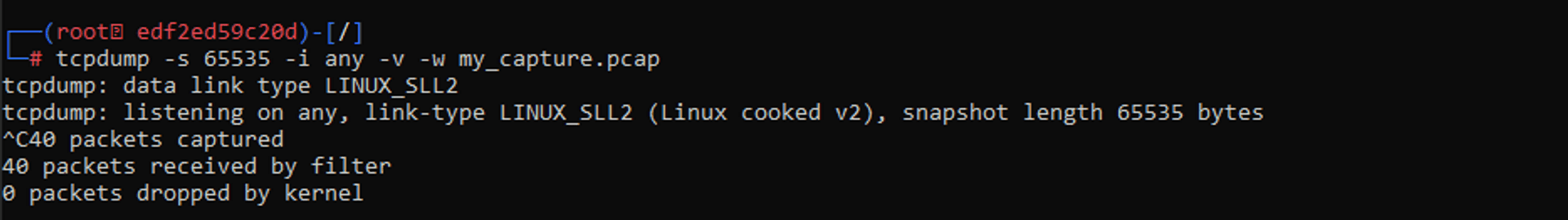
You can stop the capture with CTRL + C.
Now that we have our capture file, we can transfer it to our Desktop and read it with WireShark.
Get the ID of your Victim container with docker ps and move the file like we did with our agent:
Now it's time to download .
WireShark is a great network protocol analyzer and will let us see deep into our captured conversations.
When you install it, open the my_capture.pcap file.
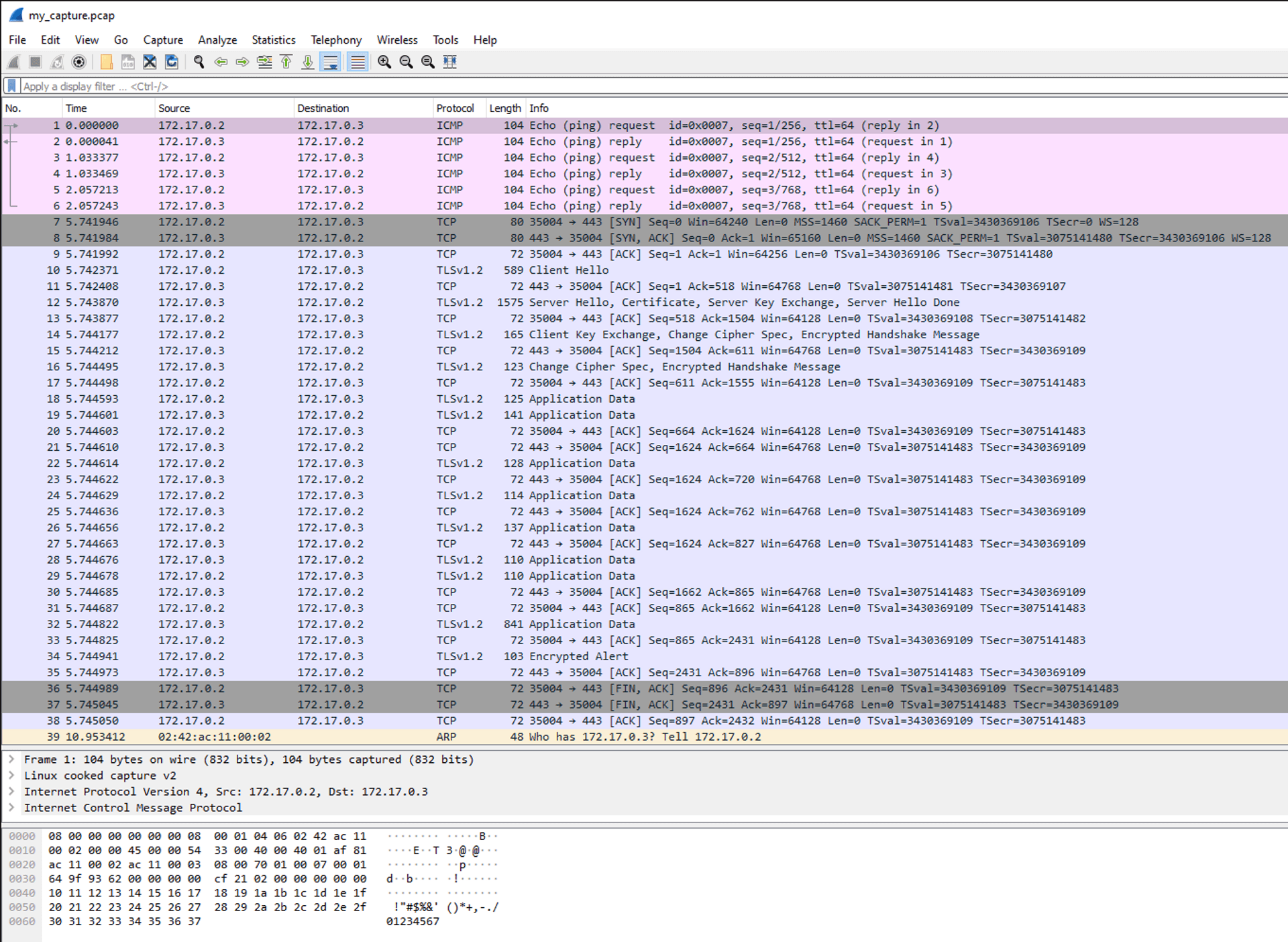
You can see so many cool things!
Ping sends a request and then receives a reply!
You can see the handshake happen when we curled the reverse-proxy server, and the key exchange!
We can even inspect the encrypted packets!
Truly WireShark is a marvel.
Previous step Time for RAT.
Next step Running a scenario.
Published